The UK’s National Cyber Security Centre (NCSC) handled a record number of cyber security incidents over the last year, according to its annual review, which is published today.
The agency handled 723 serious incidents between last September and the end of August – a 20% increase on the 602 it handled the year before. More than 200 of these incidents were related to the coronavirus.
Earlier this year the NCSC warned that bogus emails posing as communications from health authorities were being sent with links claiming to provide important updates, which when clicked instead lead to devices being infected with malware.
Other issues the agency and the government have warned of include attacks from state-sponsored hackers, including the Russian Federation, attempting to spy on the UK’s vaccine research.
Three years after the WannaCry ransomware attack, and with the NHS facing exceptional amount of strain due to the pandemic, the NCSC was directed by the Department of Health and Social Care to check the security of NHS IT systems.
It examined more than a million IP addresses across the NHS IT estate, leading the agency to identify 160 high-risk and critical vulnerabilities that attackers could have exploited to disrupt clinical care.
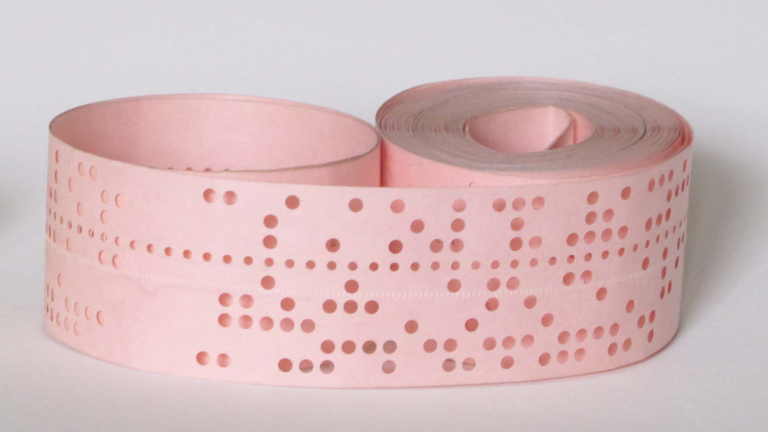
The annual review also revealed that one of NCSC’s sub-departments, the UK Key Production Authority (UKKPA) celebrated a very delayed success this year in moving an old (if very secure) paper-based system into the digital world.
UKKPA is responsible for creating and distributing the cryptographic keys used by the military and other organisations in the UK which need to communicate with an exceptional level of protection.
For a long time, these keys have been printed on spools of punched paper tape which are physically transported in protected canisters to battleships and other very sensitive locations.
As reported by Computer Business Review, which revealed that the paper tape was still being used last year, it has been hard to replace because it has such a crucial function across “a sweeping range of secure infrastructure, including the cockpits of fighter jets, military radios, and submarines”.
Now, according to the annual review, the UKKPA has developed a replacement method by producing these keys “in an electronic, highly secure format, meeting the advanced requirements of national and international defence partners”.
NCSC also stated it “played a bigger role than ever in defending the UK’s democratic processes”, and issued “specific guidance on how to respond to targeted phishing attacks” to more than 200 prominent figures, including government ministers.
Despite this guidance, the report acknowledged that the government has accused Russian actors of interfering in the 2019 General Election, when they had amplified access to trade documents subsequently cited by Jeremy Corbyn during an election debate.
The NCSC declined to respond to questions about whether the agency had done enough to defend the UK’s democratic processes in the light of reports that the trade papers used to interfere in the election were stolen from Liam Fox’s email inbox.
The agency’s new chief executive, Lindy Cameron, said the annual review outlined “the breadth of remarkable work delivered by the NCSC in the past year, largely against a backdrop of the shared global crisis of coronavirus.
“From handling hundreds of incidents to protecting our democratic institutions and keeping people safe while working remotely, our expertise has delivered across multiple frontiers.
“This has all been achieved with the fantastic support of government, businesses and citizens and I would urge them to continue contributing to our collective cyber security.”